In a statement shared by Metaverse Post, Chris Were asserts that ZK-based privacy technologies will herald a transformative phase in software architecture.
In Brief
Chris Were, head of Verida, emphasizes the importance of user empowerment, robust encryption, and the application of zero-knowledge proofs to combat the dangers of data breaches.

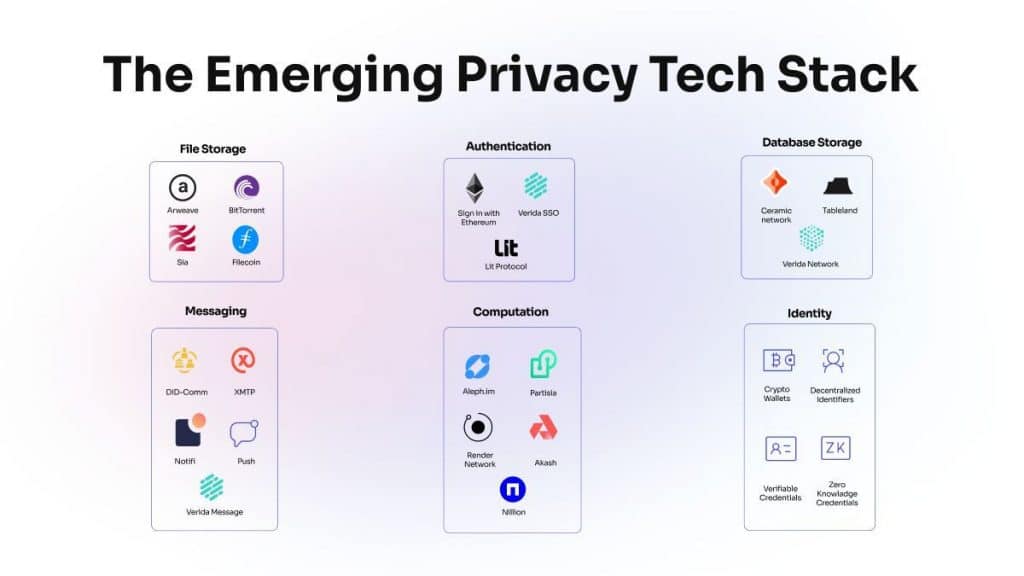
Currently, there are rising concerns regarding data security and privacy infringements within centralized systems, which often involve multiple layers and include numerous personnel that have diverse access privileges. The majority of cyber-attacks result from social engineering tactics aimed primarily at staff members. data breaches This growing apprehension has led to the emergence of privacy-centric technology stacks in the realm of cybersecurity, providing superior control and protection for users and enterprises alike.
During a discussion with Metaverse Post, he pointed out that the privacy tech stack symbolizes a substantial shift that can initiate a new era in software engineering, where user authority, data integrity, and privacy are of utmost importance.
Verida is a comprehensive development platform and a decentralized network focused on personal data management. Chris Were , CEO of Verida Imagine a data breach occurring in a traditional platform; it’s much like a burglar infiltrating a home and stealing everything, compromising the data of every single user involved. This is a critical concern since a single weakness can jeopardize everyone’s information. On the other hand, with the new privacy technology stack, information is decentralized, existing with individual users. Thus, if a breach occurs, it impacts only one individual, making the fallout much more contained and manageable,” Chris Were explained to Metaverse Post.
“It’s crucial to recognize that many hacks originate from stolen passwords. The upcoming privacy tech stack seeks to eliminate passwords, replacing them with more complex encryption keys and private keys that are incredibly difficult to crack. This transition, along with the removal of passphrases and security queries, significantly boosts the overall security and privacy for users,” he continued. Web3 .
An essential feature of the privacy tech stack is its focus on decentralized identity management, which guarantees that users maintain exclusive control over their personal data, using a unique private key for each individual. This evolution empowers users and lays the groundwork for more consistent and transparent digital engagements.
The Role of Zero-Knowledge Proofs within the Privacy Tech Stack
Zero-knowledge proofs stand as a fundamental aspect of the privacy tech stack, allowing users to offer only the information absolutely necessary to utilize a service. This approach employs cryptographic techniques to minimize the chances of exposing sensitive data while improving security by storing credentials in decentralized databases. secure Highlighting the relevance of this technology, Chris Were remarked, \"In today's scenario, whenever we need to validate our data, we generally have to disclose the actual information itself. For instance, if I'm trying to show that I'm of legal age, I might have to present a passport or a driver's license, disclosing extensive personal details just to confirm my age.\"
"Conversely, zero-knowledge credentials operate on a different premise. Utilizing advanced mathematical principles, they enable two parties to interact in a way that allows someone to verify their age without revealing any actual personal information, not even their identity,\" he elaborated.
Another critical element of the privacy tech stack comprises decentralized databases, which possess a unique capability to reduce cybersecurity threats relative to centralized databases. The strength of this decentralized approach comes from putting control directly in the hands of users with private keys, establishing a stronghold of security and privacy. zero-knowledge In contrast to centralized databases that necessitate implicit trust in the controlling entity, decentralized systems adopt a user-focused model. Within this framework, businesses and applications must actively seek user consent to access data, nurturing a sense of trust in digital operations. This strategy significantly counters the rampant issues of data breaches prevalent in centralized platforms, where one exploit can compromise all users' information.
Chris Were noted, \"We are currently witnessing a growing consciousness among users regarding the vulnerabilities that their data faces online, including hacking threats and data security breaches. This heightened awareness will encourage users to carefully consider the products and services they choose to interact with.\"
"Security is typically an intriguing aspect that often goes unnoticed until it spirals into a problem. Forward-thinking firms are venturing into this newly decentralized framework, seizing the chance to gain a competitive advantage over those who may fall victim to security breaches,\" he remarked.
As applications continue to gain traction, users are becoming increasingly aware of the significance of retaining control over their data. The demand for applications that enhance user data accessibility and utility is anticipated to grow.
Please be aware that the information shared on this page does not qualify as and should not be interpreted as legal, tax, investment, financial advice, or any other form of guidance. It is crucial only to invest what you can afford to lose and to seek independent financial consultancy if you have uncertainties. For more information, we recommend checking the terms and conditions alongside the help and support resources offered by the issuer or advertiser. MetaversePost is committed to providing accurate and unbiased news coverage, however, market circumstances may change without prior notice. data privacy Kumar is a seasoned technology journalist who specializes in exploring the dynamic intersections of AI/ML, marketing technology, and emerging sectors such as cryptocurrency, blockchain, and NFTs. With more than three years in the field, Kumar has built a notable reputation for crafting compelling stories, conducting insightful interviews, and offering detailed analysis. Kumar's skills are focused on producing high-impact content, including articles, reports, and research papers for established industry platforms. With a distinct ability that fuses technical expertise with storytelling, Kumar excels at translating complex technological ideas into clear and captivating narratives for a diverse audience.
Blum marks its one-year anniversary by celebrating its accolades as the ‘Best GameFi App’ and ‘Best Trading App’ at Blockchain Forum 2025.
Resolving DeFi fragmentation: How Omniston enhances liquidity on TON.
Vanilla unleashes 10,000x leverage super perpetuals on the BNB Chain.
New Report
Opinion Technology Solv Protocol, Fragmetric, and Zeus Network come together to introduce FragBTC: Solana’s premier yield-generating bitcoin product.


