With the global rise in smartphone users, we’re seeing an alarming trend: the increasing use of QR Codes is being leveraged by scammers who create QR-linked phishing scams.
In Brief
As cyber threats evolve, the use of QR codes in phishing schemes, or 'Qishing', reveals a deeper worry as attackers weave in deceptive elements to hide malicious URLs.
Despite the astonishing number of smartphone users worldwide, which has reached a striking figure, it’s worth noting that around 86% of people now possess the capability to interpret the data stored within QR codes—these squares are basically digital gateways easily read by smartphones.

The easy availability of QR code generators online has encouraged widespread use, but this trend has also raised significant concerns about the risk of phishing attacks. 6.92 billion in 2023 The flexibility and ease of use of QR codes have made them appealing to cybercriminals, who’ve found inventive ways to hide their malicious links while dodging spam detection mechanisms.
For quite some time, phishers have been embedding images in their deceptive emails, often embedding malicious scripts beneath innocent-looking visuals that trick recipients into believing they're legitimate.
While these image-driven phishing attempts might resemble standard scams, they often feature significantly compressed HTML code, making it harder for traditional filters that rely on full content analysis to catch them.
Unfortunately, in most cases, only the harmful URL becomes detectable, leaving the malicious intent hidden beneath layers of deceit.
Taking phishing to a more sophisticated level, attackers have recently adopted the use of QR codes in a strategy dubbed 'Qishing' to obscure their true malicious links.
Researchers have been investigating this disturbing trend and examining how cybercriminals manipulate unsuspecting users.
According to Karl Sigler, a Threat Intelligence manager at Trustwave SpiderLabs, 'Qishing allows criminals to disguise their harmful URLs within QR codes. We've noticed that many samples pretending to be MFA notifications trick users into scanning the QR codes with their smartphones, leading them instead to phishing sites.'
Security services firm Trustwave SpiderLabs When Scanning QR Codes, Stay Vigilant and Aware
As cybercriminals continue to exploit widely used technologies, whether it's for checking restaurant menus or using payment apps like Venmo, the public tends to trust QR codes far too easily.
According to Sigler at Trustwave SpiderLabs, 'We’ve seen Qishing attacks utilizing customized templates aimed at specific organizations, effectively increasing the chances that the email will be seen as credible. The use of the victim's company logo or that of a business partner can make the scam even more persuasive.'
Attackers are adapting their tactics to focus on particular companies, crafting tailored approaches that often include the logos of the victim organizations, lending an air of legitimacy to their schemes.
'These tactics are designed to lower the skepticism that recipients may have,' Sigler explains. 'If it appears to be an email from a recognized business, users might be more inclined to open it and engage with it.'
Cybercriminals are embedding hazardous links within QR codes that often resemble steps in multi-factor authentication processes, drawing victims in with the promise of access.
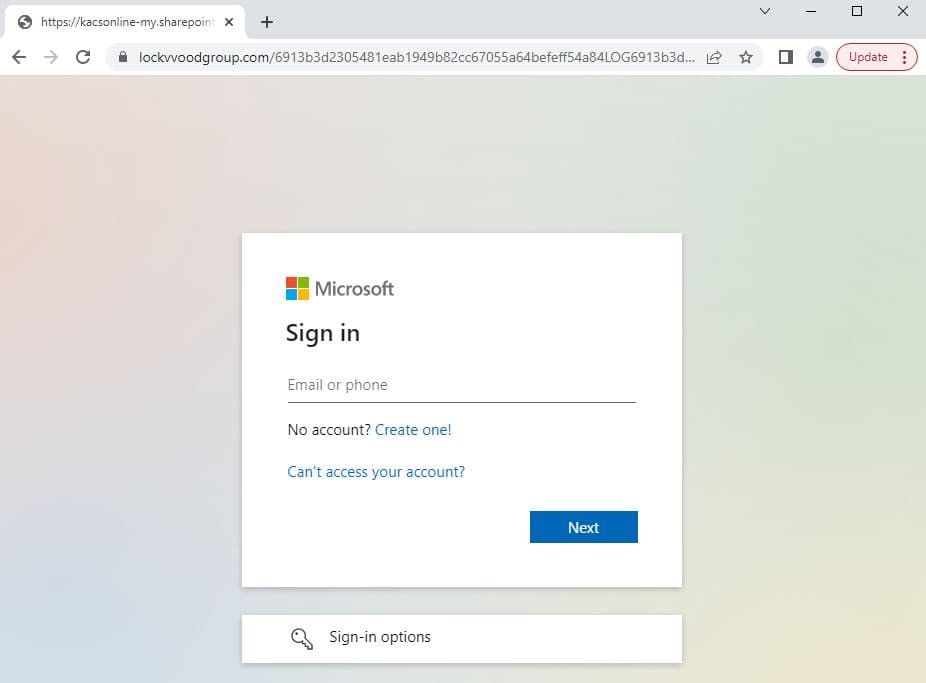
However, instead of leading to the anticipated website, these QR codes reroute victims to pages set up by the attackers for phishing.
These malicious QR codes are also found hidden within PDF attachments in deceptive emails, which entice recipients to open the documents containing the harmful QR codes.
'Many people still trust PDF files, believing they are safe. While some email security protocols can scan Office documents for threats, PDFs pose a different challenge,' says Sigler. 'Since QR codes are just images within those documents, scanning them usually results in no suspicious content being flagged.'
In one observed sample, an email was entirely devoid of body text, instead urging recipients to open an attached PDF file which concealed the malignant QR code. This method significantly boosts the email's ability to bypass anti-spam filters.
Similarly, some phishing emails incorporate HTML attachments that contain QR codes. When victims access the HTML file, they are encouraged to scan the QR code within, leading them to phishing websites.
Phishing page imitating Microsoft’s Single Sign-On process.
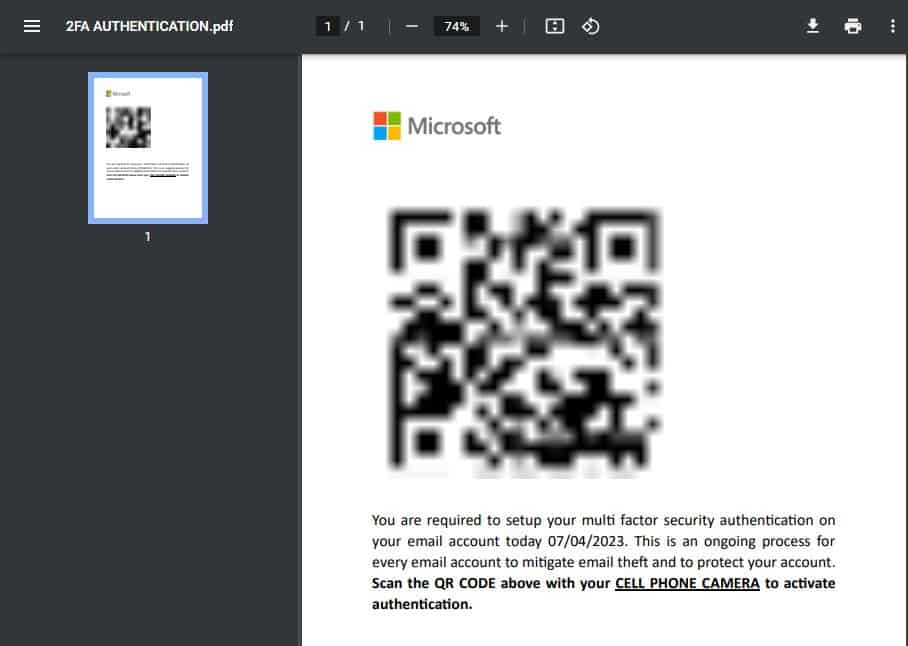
The QR codes used in these scams are often generated dynamically through APIs like those from qrserver.com, which allows attackers to customize each QR code for their specific phishing operation.
Awareness and Risk Management for Qishing
To combat these evolving threats, it’s essential to focus on raising awareness and investing in comprehensive cybersecurity training.
'Increasing awareness is critical for safeguarding ourselves against these risks. Organizations must emphasize the importance of training employees to be more cautious when reviewing unexpected emails and to implement robust security measures to defend their infrastructure,' Sigler shared with Metaverse Post.
'Honestly, unless it’s something like an email signature, there’s really no good reason to have a QR code in an email. If you ever find a QR code in an email, just don’t scan it. This is particularly important for emails where the sender explicitly asks you to scan the code.'
Please note that the information provided here is not meant to serve as legal, financial, investment, or any other form of advice. It’s crucial to only invest what you can afford to lose and to consult with independent financial advisors if you have any uncertainties. For further information, we recommend checking the terms and conditions as well as the support resources provided by the issuer or advertiser. MetaversePost is committed to delivering accurate and unbiased reporting, but keep in mind that market conditions can change rapidly.
Victor, who serves as a Managing Tech Editor/Writer for Metaverse Post, focuses on areas like artificial intelligence, cryptocurrency, data science, the metaverse, and cybersecurity for enterprises. With five years of experience in media and AI, he has worked for notable publications such as VentureBeat, DatatechVibe, and Analytics India Magazine. As a Media Mentor at prestigious institutions like Oxford and USC and holding a Master’s degree in data science, Victor is dedicated to staying updated on emerging trends.
Disclaimer
In line with the Trust Project guidelines He brings readers the latest and most insightful stories from the Tech and Web3 realms.







