PassGAN: The Innovative AI Capable of Breaking Passwords in Under 30 Seconds
In Brief
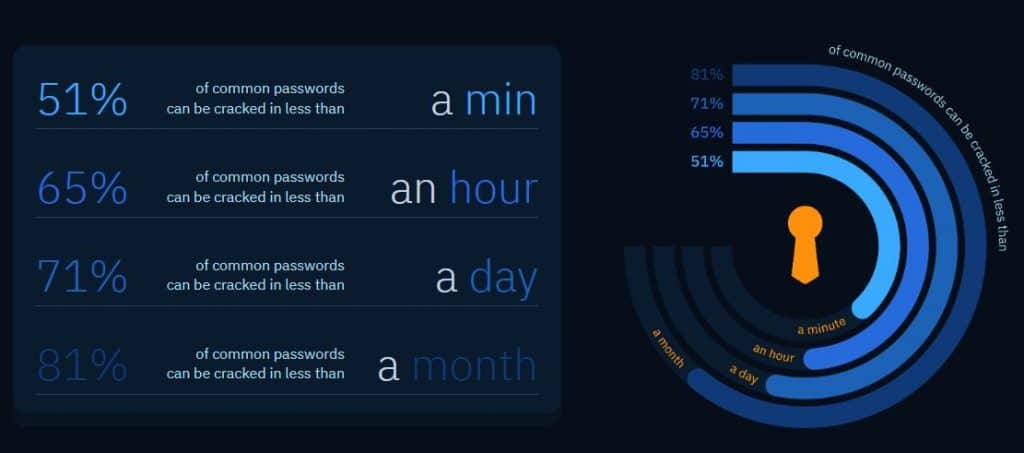
The PassGAN AI, engineered by Home Security Heroes, showcases an alarming capability to decode passwords in less than thirty seconds. Impressively, it can crack 65% of passwords within an hour, 71% within a day, and a staggering 81% within a month.
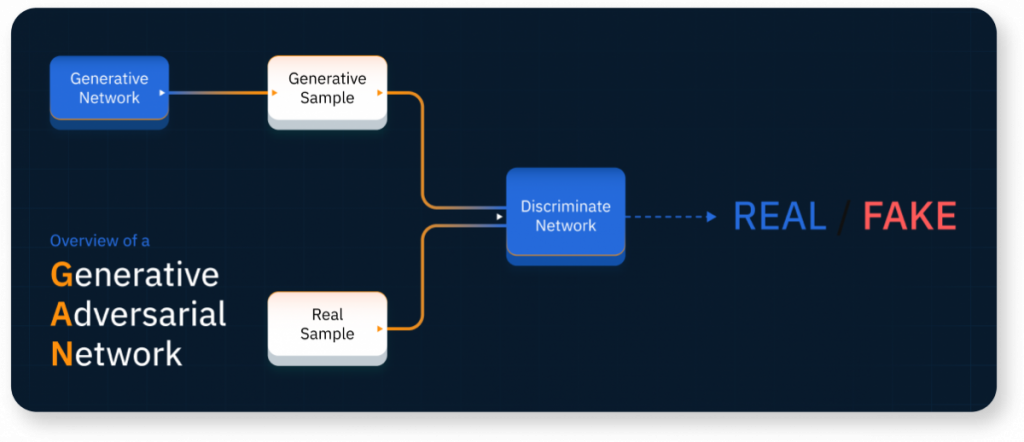
The emergence of PassGAN marks a significant shift in password cracking techniques, as it eliminates the need for manual password scrutiny. Instead, it harnesses a Generative Adversarial Network (GAN) that autonomously captures the patterns found in leaked passwords.
With PassGAN’s sophisticated tracking of various password characteristics, the AI enhances the success rate of guessing passwords, putting your sensitive information at risk.
The realm of Artificial Intelligence (AI) is rapidly progressing, prompting capabilities once considered fantasy to become reality. One such example is this: PassGAN developed by a research team from Home Security Heroes. This AI exhibits a terrifying efficiency: capable of cracking passwords in less than thirty seconds, far exceeding the speed of human analysts or conventional methods.

Home Security Heroes released a report detailing PassGAN's alarming efficiency regarding password security. Their findings revealed that 51% of passwords were cracked in less than a minute, 65% within an hour, 71% in one day, and 81% within a month. This rise of AI technology leaves individuals struggling to maintain password security.
PassGAN's rapid cracking speed can be attributed to its ability to analyze genuine passwords from actual data leaks. It’s programmed to discern the common patterns in passwords, allowing it to make significantly quicker and more precise guesses.
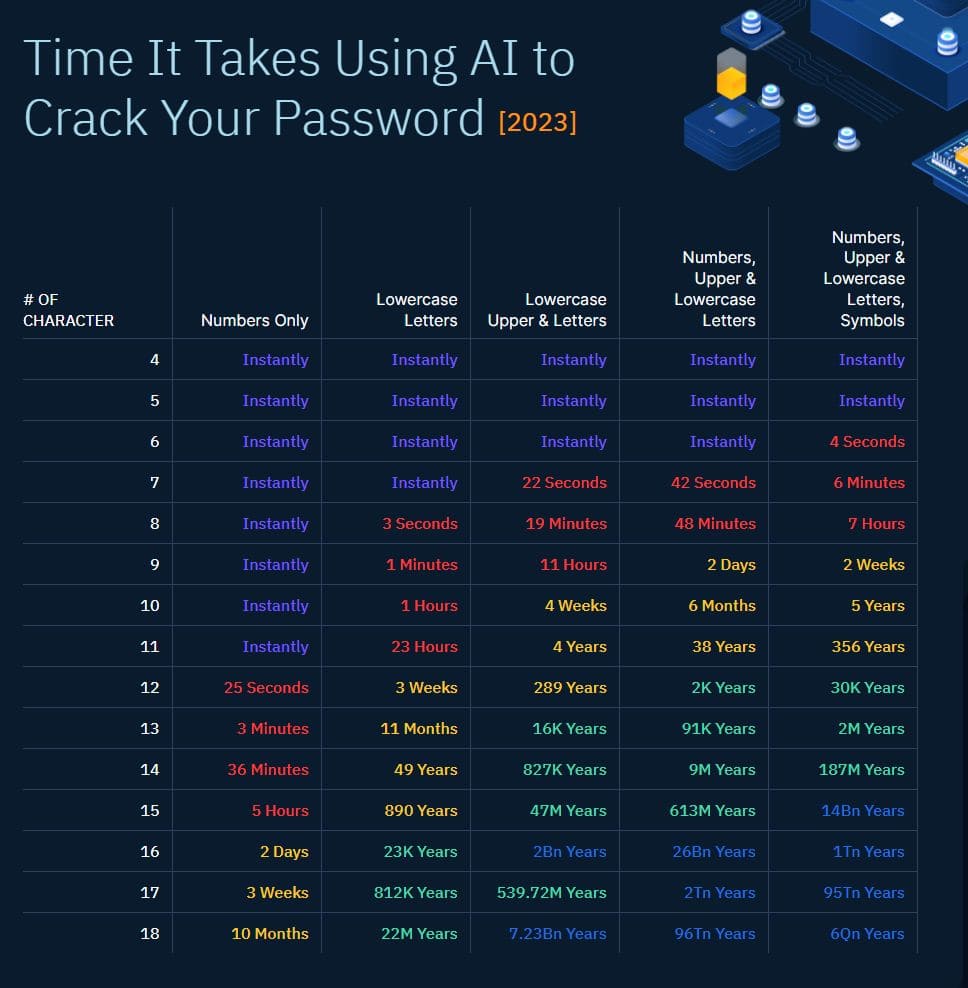
To grasp this capability, consider that PassGAN can sift through an astonishing 15,600,000 commonly used passwords and determine how quickly it could crack your specific password in under six minutes. Typically, passwords longer than 18 characters are considered secure against AI-based attacks; for instance, number-only passwords might take around ten months, while combinations of symbols, numbers, and letters could take 6 quintillion years to break.
The advent of PassGAN represents a troubling evolution in password-cracking techniques. This latest approach eliminates traditional password analysis through a Generative Adversarial Network (GAN), which learns the nature of real passwords from breaches. While this innovation increases the effectiveness of password cracking, it significantly endangers online security.
With its ability to offer multiple characteristics of passwords and project possible password quality, PassGAN simplifies the process for potential hackers trying to compromise your personal data. It is crucial to regularly update your passwords to shield yourself from such advanced password-cracking technology.
Understanding the foundation of modern password-guessing techniques is vital to grasping how PassGAN functions. Generally, password-cracking software employs straightforward data-driven methods. This means they rely on techniques to analyze passwords manually. Moreover, these tools utilize password construction strategies such as concatenation and make various assumptions based on password trends. data models These password-guessing methods typically excel with simple and predictable passwords. However, they tend to become inefficient or completely unable to crack more complex password patterns when faced with larger sample sizes. This is where systems like PassGAN come into play.
These systems train computers to interpret and assess data similarly to human cognitive processing. The neural networks utilized by GAN are designed to capture a range of structures and features. Training for PassGAN involved the RockYou dataset, which served as a foundation for developing intelligent systems in password analysis. After training, the GAN can leverage the acquired knowledge to generate new password examples that align with observed distributions.
Systems called neural networks What Are the Best Practices to Secure Your Passwords?
Ensuring the confidentiality of your passwords is of utmost importance. Unfortunately, numerous instances of leaked password databases reveal that many individuals tend to use uncomplicated and predictable passwords. So, how can you fortify your password to guard against cyber threats? Let’s explore several strategies.
The fundamental difference between a robust password and one that's easily cracked lies in its strength. With data acquired from PassGAN password samples, researchers found that a digit-only password with ten characters can be compromised in a matter of seconds. top password security options.
While a ten-character password combining both uppercase and lowercase letters could take four weeks to crack, a ten-letter password consisting solely of lowercase letters would be vulnerable within an hour. In contrast, a solid ten-character password featuring a mix of letters, symbols, and numbers would require about five years to break.
Regularly updating your passwords every three to six months is a proactive step in safeguarding your accounts. If you suspect that someone may have accessed your account or that you may have inadvertently shared your password, it’s essential to change it immediately to prevent unauthorized access.
Changing your password It is evident that traditional password cracking techniques are no match for PassGAN. This AI can effortlessly compromise any password in less than thirty seconds, underscoring the need for individuals to adopt strong password protective measures. With AI technologies continuously evolving and improving, maintaining password security will only become more challenging.
While AI has been celebrated for its potential to enhance lives, it has seemingly morphed into one of the most perilous software scams to emerge. Vall-E, a synthetic voice technology, can imitate actual individuals using recordings from real sources.
- Microsoft’s VALL-E Additionally, a Microsoft code facilitates its function, enabling fraudsters to exploit it to fleece people by pretending to be someone they’re familiar with. person’s voice Experts in Finland predict that attackers will soon leverage AI to execute particularly effective phishing campaigns. WithSecure, alongside the Finnish Transport and Communications Agency and the Federal Emergency Management Agency, has released a report analyzing the intersections of AI, cyber threats, and developments in the field. The use of AI in cyber attacks is especially potent when it comes to impersonation strategies frequently deployed in phishing and vishing scams. Cybercriminals are already harnessing AI to automate their operations and manipulate ChatGPT chatbots for social engineering tricks. friend’s voice or the voice of a celebrity.
- The Risks of Artificial Intelligence: Projected Uses of ChatGPT by Cybercriminals in the Upcoming Years
Read more about AI:
Disclaimer
In line with the Trust Project guidelines Damir leads the team as the product manager and editor for Metaverse Post, focusing on topics like AI/ML, AGI, LLMs, the Metaverse, and Web3. His writing resonates with a broad audience, attracting over a million users monthly. With a decade of experience in SEO and digital marketing, Damir has contributed to reputable platforms like Mashable, Wired, Cointelegraph, The New Yorker, Inside.com, Entrepreneur, BeInCrypto, and more. Traveling between the UAE, Turkey, Russia, and the CIS as a digital nomad, Damir holds a bachelor's degree in physics, which he believes equips him with critical thinking abilities essential for thriving in the ever-evolving online environment.







