Crypto Heists: Understanding How Digital Currency Gets Stolen and the Role of Authorities in Recovering Assets
In Brief
The instances of cryptocurrency theft are escalating due to scams, hacking incidents, and fraudulent activities. However, swift action, blockchain analysis, and collaboration with law enforcement are essential for retrieving lost assets.

As the cryptocurrency landscape continues to grow, so do the threats accompanying it — scams, hacks, and phishing attempts have transitioned from rare occurrences to common issues that many face daily.
While blockchains tout transparency, the decentralized essence of cryptocurrencies can actually be a disadvantage when funds are misappropriated. With no customer service lines to call for help, victims frequently find themselves stranded in a system that even law enforcement is still figuring out how to navigate.
In this article, we will delve into the prevalent methods of cryptocurrency theft today, the challenges in reclaiming misappropriated funds, and how specialized teams are aiding law enforcement in tilting the scales back in favor of victims.
Common Cryptocurrency Fraud Schemes in 2024-2025
Wallet Drainers – Exploitation Scams Targeting Digital Wallets
Wallet drainers aren't brute-force attackers; instead, they operate stealthily—designed to trick users into relinquishing their assets knowingly.
The strategy is typically the same: lure victims to a counterfeit site, have them connect their wallets, and approve transactions they might not entirely grasp. That one authorization? It's all that’s required for the attacker. Some variations go further by embedding harmful code in fake browser add-ons or masquerading as 'helpful' wallet applications. Even a single use can mean your private keys are compromised.
Case Study: Angel Drainer + Image
One of the most notable tools to emerge in 2024 was Angel Drainer, which facilitated the theft of over $25 million from more than 35,000 wallets.
An investigative effort by Match Systems followed the trail using off-chain clues, including reused servers and shared browser fingerprints, ultimately identifying the group responsible. This led to a significant victory in the battle against wallet drainers, resulting in complete exposure and disruption of their operations.
Address Poisoning – A Tactic for Tampering with Transactions
It often only takes a single misclick to cause chaos.
Address poisoning is a straightforward yet impactful scam where criminals insert a fraudulent wallet address into your transaction history, banking on the possibility that you might mistakenly select it.
They transmit a minuscule amount of cryptocurrency from an address that is nearly identical to a trusted one. This counterfeit appears in your transaction logs, and later, when you're in a rush to send funds… wham! You paste the wrong address, and your money vanishes. This is one of the most cost-effective scams to execute, and it's notoriously difficult to reverse.
Case Study: Recovery of $68M from Address Poisoning
In 2024, Match Systems We successfully tracked a hacker who employed this very technique to siphon off $68 million.
This rogue actor avoided KYC-compliant exchanges and made efforts to mask their identity — yet investigators dug deeper. They analyzed IP logs, correlated device fingerprints, and investigated wallet movement patterns. The final outcome? A complete recovery of funds, sending a strong warning to would-be scammers: blockchain forensic techniques are always on the lookout.
Exchange and Platform Hacks
Exchanges are a hacker's prime target — that's where the substantial funds reside.
With billions in user deposits secured across both hot and cold wallets, primarily gated by some layers of security codes and credentials, just a single weak point can create avenues for attack. Many breaches follow predictable paths: phishing attempts, compromised admin access, and overlooked vulnerabilities. Yet when breaches occur, they can lead to significant financial losses.
Here's a glimpse into some of the largest exchange hacks from 2024 and 2025 — each incident serves as a stark reminder that even the leading platforms are not infallible.
Case Study: Bybit Hack — February 2025
One of the most significant cryptocurrency thefts on record took place when attackers infiltrated Bybit's cold wallets, making away with roughly $1.5 billion, which included over 400,000 ETH.
Investigators connected this operation to North Korea's Lazarus Group, a name that recurs whenever there are high-stakes, precision breaches. A flaw within DMM Bitcoin's internal system permitted hackers to extract approximately
Case Study: DMM Bitcoin — May 2024
This breach precipitated global inquiries and heightened scrutiny regarding the security measures exchanges employ across their backend. $305 million, or close to 4,500 BTC.
India's largest exchange suffered a nearly $234.9 million loss due to vulnerabilities in its multi-signature wallet architecture.
Case Study: WazirX — July 2024
Investigations highlighted structural weaknesses that enabled the attack.
Multiple reports , including one by Halborn Attackers breached BtcTurk’s hot wallet infrastructure, draining roughly $55 million in digital assets.
Case Study: BtcTurk — June 2024
Despite a rapid response from the exchange, the divided nature of the stolen funds across various wallets made recovery significantly more challenging. A coordinated assault struck BingX’s hot wallets, and while details are still surfacing, preliminary findings suggest possible compromise of internal credentials.
Ponzi Schemes & Phony Investment Platforms
Case Study: BingX — September 2024
uk These scams have essentially never gone away; they’ve merely updated their branding. uz
In the crypto world, fraudulent investment platforms are ubiquitous. They feature eye-catching interfaces, guarantees of daily returns, and Telegram admins posing as customer service. Everything appears legitimate—until it abruptly comes to a halt.
When the influx of new investors dwindles, the platform turns mute. Withdrawal requests freeze, and soon, the website disappears. As for the funds? They’re typically long gone by then.
Retail investors frequently bear the brunt of these scams. With the anonymity of most of these operations and the absence of genuine points of contact, reclaiming lost funds becomes nearly impossible.
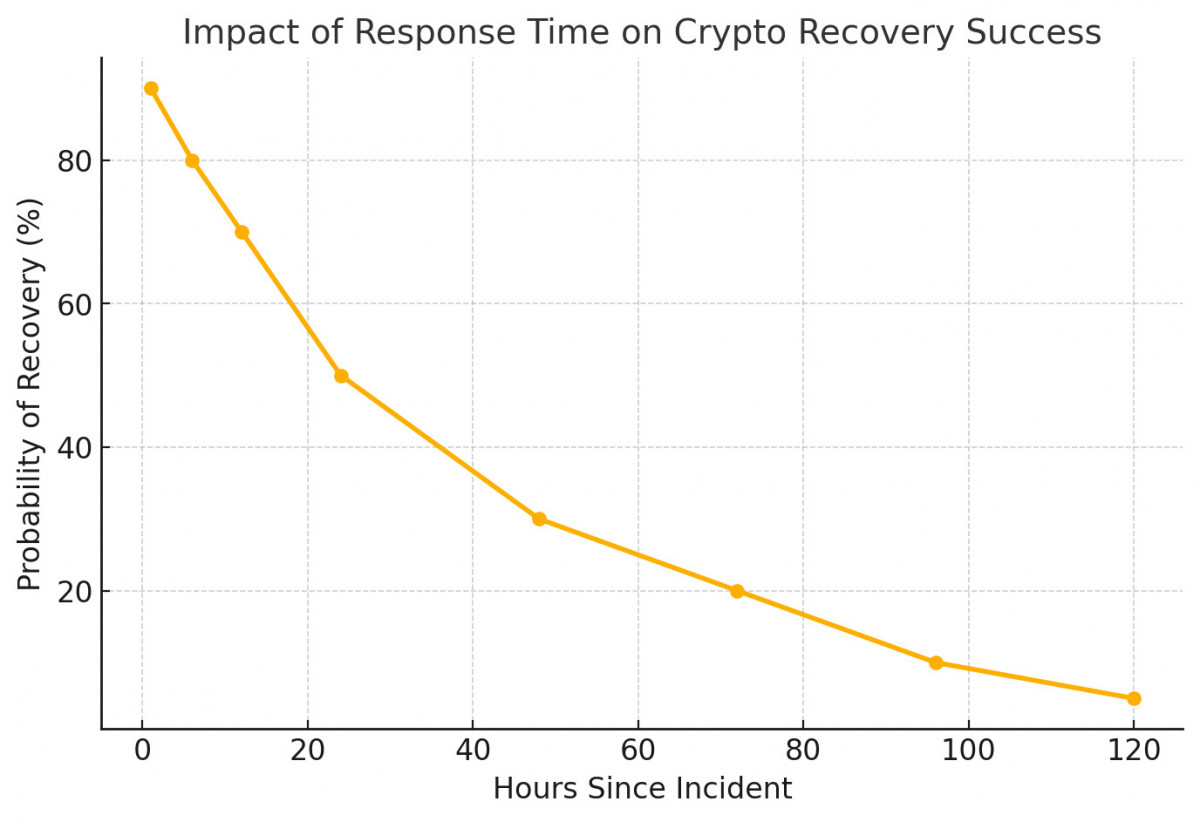
Why Timely Action Is Crucial in Crypto Recovery
When cryptocurrency vanishes, delay works to the hacker's advantage. Perpetrators don’t hold onto stolen assets for extended periods; they act swiftly — dispersing funds across different wallets, funneling them through mixers, or cashing out before anyone notices. After a day or two, following the trail becomes increasingly difficult. Sometimes it disappears entirely.
Investigators suggest that the recovery window significantly diminishes within the first 24 hours post-theft. Following that, the chances of success plummet sharply, turning the likelihood of a full recovery from slim to virtually non-existent.
That’s why a prompt response is vital. It's about more than submitting a report; it’s crucial to have experienced professionals on the case as soon as possible. Every second is essential.
How Match Systems and Other Private Companies Aid Law Enforcement
Private investigative agencies are vital in supporting law enforcement in cryptocurrency-related investigations.
Using tools like those from Match Systems, Chainalysis, TRM Labs, and Elliptic to analyze blockchain transactions, they can trace illegal activities and pinpoint the wallets of criminals. Forensic investigations delve deep into cybercrime activities.
Collaboration with law enforcement agencies entails providing assistance in running investigations, compiling detailed reports, and offering expert insights on cases of cybercrime. They also guide law enforcement in formulating legal requests for freezing assets held by Virtual Asset Service Providers (VASPs).
The landscape of crypto-related crime is continually changing — and so do the methods to combat it.
uz
Recovering assets successfully requires more than just on-chain transparency; it hinges on quick action, access to sophisticated forensic tools, and seamless coordination between public authorities and private sector experts. While law enforcement plays an essential role in many cases, they increasingly depend on external specialists for support. vi The lesson is simple: the quicker the response, the less chances attackers have of succeeding.
, please be aware that the information presented on this page is not meant to serve, and should not be construed as, legal, tax, investment, or financial advice of any kind. It's vital to only invest what you can afford to lose and to seek independent financial counsel if you're uncertain. For additional details, we recommend consulting the terms and conditions and the help and support resources provided by the issuer or advertiser. MetaversePost remains dedicated to delivering accurate, impartial reporting, but market conditions may shift without prior notice.
Victoria adeptly covers a range of topics in technology, including Web 3.0, artificial intelligence, and cryptocurrencies. Her vast experience empowers her to create insightful articles designed for a broader audience.
Cryptocurrencylistings.com Launches CandyDrop to Streamline Crypto Acquisition and Boost User Engagement with Quality Projects
DeFAI Must Address Cross-Chain Challenges to Realize Its Full Potential
Metaverse Post
Featured Metaverse Post dRPC Introduces NodeHaus, a Platform Designed to Enhance Blockchain Access for Web3 Foundations


