Circle STARKs Introduced: Buterin’s New Development Holds the Key to Solving the Blockchain Scalability Challenge.
In Brief
Vitalik Buterin, one of the masterminds behind Ethereum, has unveiled Circle STARKs, a new cryptographic solution designed to improve both the security and efficiency of blockchain technology, while addressing the weaknesses of earlier STARK implementations.

Vitalik Buterin, a key figure in the formation of Ethereum, has formulated a cutting-edge cryptographic tool known as Circle STARKs that aims to boost both the reliability and efficiency of blockchain systems. This innovative approach addresses and rectifies the limitations seen in previous STARK frameworks. a shout-out to my friends for their gracious support in wrapping my head around these complex ideas!
Narrower cryptographic fields, particularly, are at the core of Circle STARKs and signify a significant pivot away from the conventional 256-bit fields that were common in earlier STARK protocols. While larger fields offered greater security, they often resulted in sluggish proofing rates and computational inefficiencies. By shifting to Mersenne31, we can achieve considerable performance gains.
That said, limited fields come with their own set of challenges as they offer a narrower set of possible values, potentially introducing security vulnerabilities. To tackle this challenge, Buterin’s team employs extension fields alongside various random tests. This approach broadens the range of values an adversary would need to navigate, leveraging the efficiency of smaller fields while creating a computational barrier that upholds the validity of the protocol. Mersenne31 Mersenne31 allows for efficient arithmetic operations that utilize current 32-bit CPU/GPU capabilities, resulting in arithmetic operations that can be notably more productive—about 1.3 times more—the other smaller field protocols.
Fast Reed-Solomon Interactive Oracle Proofs of Proximity (FRI)
Within Circle STARKs, FRI serves as a critical mechanism to ensure that functions adhere to polynomial characteristics. This layer adds security to the protocol, ensuring that it dismisses any proofs generated from non-polynomial inputs. BabyBear Circle STARKs fine-tunes the FRI process for maximum efficiency. By organizing polynomial assessments through a modified reverse bit sequence, the protocol increases its space efficiency while also enabling more robust Merkle proofs. The folding structure within Circle STARKs is specifically designed to harmonize with this ordering method.
The classic FRI domain reduction process involves squaring the multiplicative subgroup elements through a two-to-one mapping. In contrast, Circle FRI introduces an innovative method by operating on point pairs (x, y) that satisfy the equation x^2 + y^2 = 1 mod p. This new structure allows for a unique folding technique that maintains the necessary qualities for swift proof generation.
The Circle FRI approach begins with consolidating all points to a single line. It then reduces domain size by selecting random linear combinations. Each iteration essentially halves the set size due to the application of a new mapping. This cycle continues until the polynomial degree is manageable enough for direct verification.
Striking a Balance between Efficiency and Developer Friendliness
Importantly, Buterin emphasizes that unlike traditional STARKs, Circle STARKs do not add significant complexity for developers. The protocol encapsulates much of the intricate mathematical details, enabling developers to engage with Circle STARKs without needing to completely grasp every fine mathematical point.
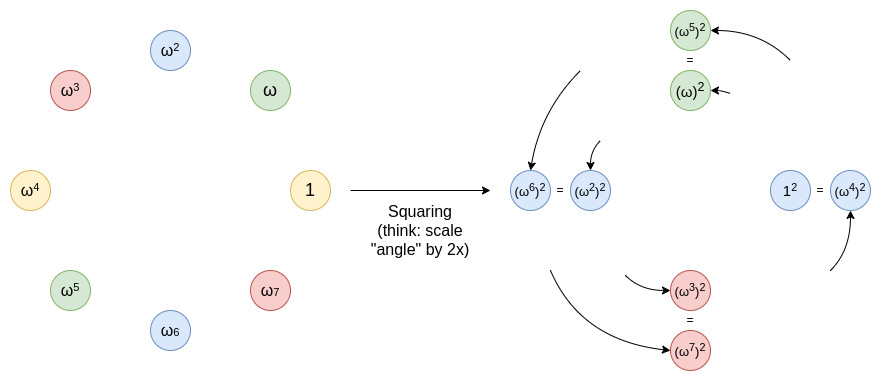
Photo: Vitalik Buterin
Moreover, the protocol features what are termed 'exotic FFTs' (Fast Fourier Transforms), which strike a sweet spot between clarity and efficiency. Circle FFTs enhance performance without the convoluted nature of elliptic curve FFTs, making them accessible for both researchers and developers. The community's acceptance and subsequent advancement of this protocol might greatly hinge on its user-friendliness.
Photo: Vitalik Buterin
Photo: Vitalik Buterin
Round Polynomials modeled on the circular equation x^2 + y^2 = 1 can be understood as polynomials situated within what mathematicians classify as a Riemann-Roch space, where FFTs are applied. This structuring sustains the vital mathematical properties required for secure cryptographic proofs while facilitating efficient calculations.
Consequences for Blockchain Scalability and Security
Circle STARKs directly confront critical concerns related to the security and scalability of ledgers. As blockchain technology penetrates various sectors, the need for protocols capable of managing larger transaction volumes while maintaining strong security guarantees has surged.
Photo: Vitalik Buterin
The efficiency that Circle STARKs introduces could significantly influence the energy consumption of blockchain networks. By lowering the computational resources mandated for cryptographic proofs, this protocol may enhance the eco-friendliness of blockchain technology, especially in light of rising concerns over the energy demands of proof-of-work cryptocurrencies.
Leveraging Circle STARKs for zero-knowledge proofs could lead to more effective implementations. Given that zero-knowledge proofs are pivotal for numerous privacy-focused applications, this enhancement could catalyze broader acceptance of privacy-oriented blockchain solutions. Swift proof generation and verification could unveil new possibilities within privacy-centric systems, such as supply chain tracking, identity management, and decentralized finance.
Furthermore, Circle STARKs are likely to provide a competitive edge for layer-2 scaling solutions. By optimizing cryptographic proofs, the protocol could boost the efficiency of rollups and other layer-2 technologies, translating to enhanced transaction throughput and cost savings for blockchain users.
The introduction of Circle STARKs could significantly shift the blockchain architecture landscape. With enhanced efficiency in cryptographic proofs, there may be opportunities to embed more complex logic directly on-chain, potentially reducing the necessity for certain layer-2 scaling solutions. This could usher in a transformation in blockchain system structures and uses, paving the way for previously unattainable kinds of decentralized applications due to processing limitations.
For instance, improved STARKs could enable on-chain privacy-conscious computations that were previously too costly. This could foster new horizons for decentralized finance applications, allowing for the introduction of more intricate financial tools while ensuring user privacy.
Confronting the Scalability Challenge
Impact on Blockchain Architecture
With the advent of Circle STARKs, the notoriously tricky blockchain scalability trilemma—achieving scalability, security, and decentralization in tandem—finds a more effective approach. By boosting the efficiency of cryptographic proofs, Circle STARKs help facilitate more scalable blockchain systems without compromising security or catalyzing greater centralization. It’s essential to note that Circle STARKs alone won’t solve every facet of scalability hurdles. Additional technologies and strategies will remain necessary to tackle related challenges such as state growth and network delays.
Exploring Applications Beyond Blockchain
While the primary focus of Circle STARKs is in the blockchain sphere, their advantages might extend to other realms of cryptography and secure computing, making them beneficial across a variety of applications.
For instance, more efficient STARKs could enable complex collaborative computations while safeguarding anonymity in secure multi-party computations. This would be particularly valuable in contexts like medical research, where various stakeholders need to analyze sensitive data while keeping the core information confidential.
Circle STARKs also have the potential to enhance the efficacy of zero-knowledge proofs in verifying identity traits within digital validation scenarios, thus fostering a new wave of privacy-retaining systems. This could impact everything from government-issued digital IDs to online authentication processes.
, please remember that the information provided herein is not intended to serve as, and should not be regarded as, legal, tax, investment, financial, or any other form of advice. It is critical to invest only what you can afford to lose and to seek independent financial counsel if you harbor any uncertainties. For further details, we recommend consulting the terms and conditions, along with the support pages provided by the issuer or advertiser. MetaversePost is dedicated to delivering accurate and objective reporting, yet market conditions can shift without notice.
Victoria specializes in a diverse array of technology themes, including Web3.0, AI, and cryptocurrencies. Her widespread experience enables her to craft insightful articles that resonate with a broader audience.
Shardeum Empowers Validators and Unveils Autoscaling Mainnet Roadmap.
Bitcoin, Ethereum, Toncoin: Recap of Last Week’s Cryptocurrency Rally – Complete Update and Projections.
Disclaimer
In line with the Trust Project guidelines April 2025: Blockchain Initiatives that Captured the Most Attention.







